Nubeva TLS Decrypt on the AWS Cloud
Quick Start Reference Deployment

July 2021
Erik Freeland, Nubeva
Dylan Owen, AWS Integration & Automation team
| Visit our GitHub repository for source files and to post feedback, report bugs, or submit feature ideas for this Quick Start. |
This Quick Start was created by Nubeva in collaboration with Amazon Web Services (AWS). Quick Starts are automated reference deployments that use AWS CloudFormation templates to deploy key technologies on AWS, following AWS best practices.
Overview
This Quick Start reference deployment guide provides instructions for deploying an out-of-band, open-source monitoring stack for AWS. Launched tools come with the Nubeva Session Key Intercept (SKI) platform for TLS decryption pre-configured on the AWS Cloud. The stack includes the following open-source tools:
-
Arkime — A large-scale, open-source, indexed packet-capture-and-search system.
-
Suricata — A high-performance engine that comprises a network intrusion detection system (IDS), an intrusion prevention system (IPS), and network security monitoring (NSM).
-
Wireshark — A free, open-source packet analyzer for network troubleshooting.
-
Zeek — A powerful network analysis framework used for intrusion detection by looking at anomalous network activity to find suspicious data flows.
This Quick Start is for users who want to identify malicious activity, insider threats, and data leakage within their virtual private cloud (VPC) and Amazon Elastic Compute Cloud (Amazon EC2) instances with decrypted visibility.
| Amazon may share user-deployment information with the AWS Partner that collaborated with AWS on the Quick Start. |
Nubeva TLS Decrypt on AWS
Nubeva’s SKI architecture provides complete packet visibility of any public cloud with TLS decryption capabilities. All open-source tools in this solution are complemented by Nubeva SKI sensors, which provide additional intelligence and insight into encrypted data.
Container-based Nubeva SKI sensors are deployed on your monitored instances and capture TLS session keys as they flow through these instances. The packets are sent using VPC traffic mirrors that are analyzed and visualized by your chosen open-source tools. This flow provides clear visibility of your network traffic so you can identify unexpected network behavior, perform network analysis, and detect intrusions.
AWS costs
You are responsible for the cost of the AWS services and any third-party licenses used while running this Quick Start. There is no additional cost for using the Quick Start.
The AWS CloudFormation templates for Quick Starts include configuration parameters that you can customize. Some of the settings, such as the instance type, affect the cost of deployment. For cost estimates, see the pricing pages for each AWS service you use. Prices are subject to change.
| After you deploy the Quick Start, create AWS Cost and Usage Reports to deliver billing metrics to an Amazon Simple Storage Service (Amazon S3) bucket in your account. These reports provide cost estimates based on usage throughout each month and aggregate the data at the end of the month. For more information, see What are AWS Cost and Usage Reports? |
Software licenses
This Quick Start requires an account on the Nubeva SaaS console, as described in the Deployment Steps section later in this guide.
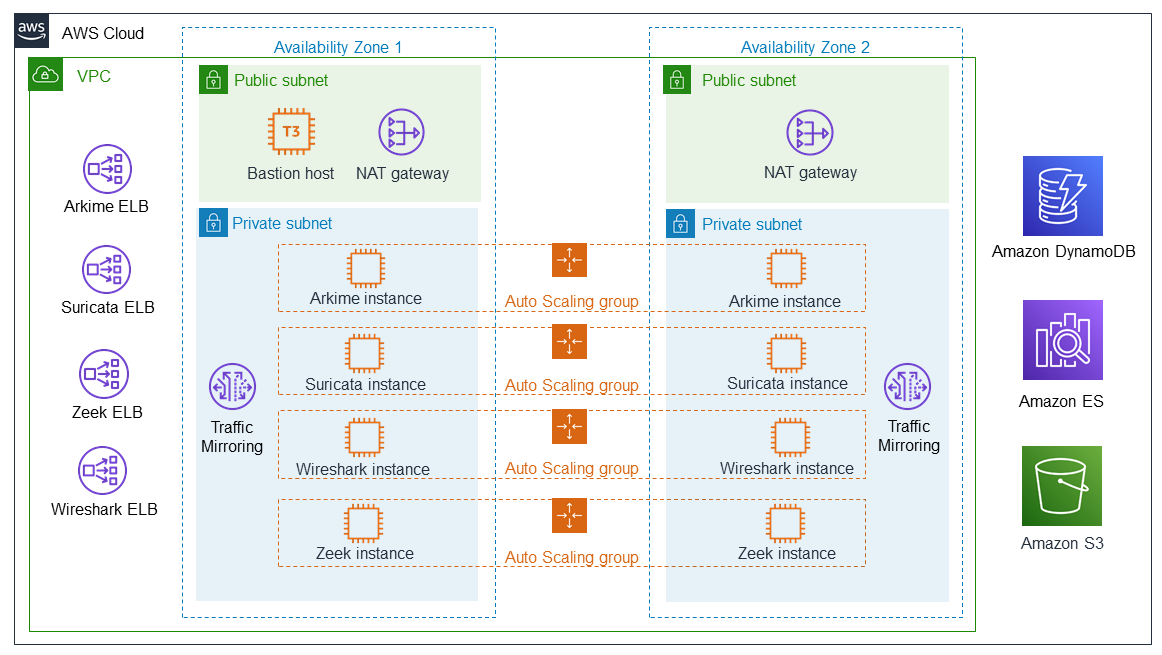
Architecture
Deploying this Quick Start for a new virtual private cloud VPC with default parameters builds the following Nubeva SKI network and security monitoring environment in the AWS Cloud.
The Quick Start sets up the following:
-
A highly available architecture that spans two Availability Zones.*
-
A VPC configured with public and private subnets, according to AWS best practices, to provide you with your own virtual network on AWS.*
-
Elastic Load Balancing (ELB) for each open-source tool to provide scaling for both tool operation and inbound packet mirroring using Amazon VPC traffic mirrors or internal replication.
-
In the public subnets:
-
A bastion host for all inbound connectivity.*
-
Managed network address translation (NAT) gateways to allow outbound internet access for resources in the subnets.*
-
-
In the private subnets:
-
Arkime packet capture in an Auto Scaling group (size 2).
-
Suricata signature detection in an Auto Scaling group (size 2).
-
Wireshark packet analysis in an Auto Scaling group (size 2).
-
Zeek anomaly detection in an Auto Scaling group (size 2).
-
Amazon VPC traffic-mirroring targets connected to each open-source load balancer.
-
A sample source instance in an Auto Scaling group (size 2) used for monitoring TLS traffic. After deployment, use the Nubeva SaaS console to add more instances to monitor. The source instance has a container-based Nubeva SKI agent deployed. This agent listens through all available interfaces & discovers TLS session keys.
-
-
Amazon DynamoDB for key storage.
-
Amazon Elasticsearch Service (Amazon ES) for managing the logs from Zeek and Suricata.
-
An Amazon Simple Storage Service (Amazon S3) bucket for Arkime packet capture (PCAP) storage.
*The template that deploys the Quick Start into an existing VPC skips the components marked by asterisks and prompts you for your existing VPC configuration.
Planning the deployment
Specialized knowledge
This deployment requires a moderate level of familiarity with AWS services. If you’re new to AWS, see Getting Started Resource Center and AWS Training and Certification. These sites provide materials for learning how to design, deploy, and operate your infrastructure and applications on the AWS Cloud.
AWS account
If you don’t already have an AWS account, create one at https://aws.amazon.com by following the on-screen instructions. Part of the sign-up process involves receiving a phone call and entering a PIN using the phone keypad.
Your AWS account is automatically signed up for all AWS services. You are charged only for the services you use.
Technical requirements
Before you launch the Quick Start, review the following information and ensure that your account is properly configured. Otherwise, deployment might fail.
Resource quotas
If necessary, request service quota increases for the following resources. You might need to request increases if your existing deployment currently uses these resources and if this Quick Start deployment could result in exceeding the default quotas. The Service Quotas console displays your usage and quotas for some aspects of some services. For more information, see What is Service Quotas? and AWS service quotas.
| Resource | This deployment uses |
|---|---|
VPCs |
1 |
AWS Identity and Access Management (IAM) security groups |
8 |
IAM roles |
6 |
Auto Scaling groups |
3 |
Elastic Load Balancers |
3 |
m5.large instances |
6 |
t3.micro instances |
3 |
DynamoDB |
1 |
Supported AWS Regions
For any Quick Start to work in a Region other than its default Region, all the services it deploys must be supported in that Region. You can launch a Quick Start in any Region and see if it works. If you get an error such as “Unrecognized resource type,” the Quick Start is not supported in that Region.
For an up-to-date list of AWS Regions and the AWS services they support, see AWS Regional Services.
| Certain Regions are available on an opt-in basis. For more information, see Managing AWS Regions. |
IAM permissions
Before launching the Quick Start, you must sign in to the AWS Management Console with IAM permissions for the resources that the templates deploy. The AdministratorAccess managed policy within IAM provides sufficient permissions, although your organization may choose to use a custom policy with more restrictions. For more information, see AWS managed policies for job functions.
Deployment options
This Quick Start provides two deployment options:
-
Deploy Nubeva SKI into a new VPC (end-to-end deployment). This option builds a new AWS environment consisting of the VPC, subnets, NAT gateways, security groups, bastion hosts, and other infrastructure components. It then deploys Nubeva SKI into this new VPC.
-
Deploy Nubeva SKI into an existing VPC. This option provisions Nubeva SKI in your existing AWS infrastructure.
The Quick Start provides separate templates for these options. It also lets you configure Classless Inter-Domain Routing (CIDR) blocks, instance types, and Nubeva SKI settings, as discussed later in this guide.
Prepare your Nubeva account
-
Navigate to https://www.nubeva.com, and choose Login from the main menu.
-
First-time users are prompted to create an account. You can use one of the OAuth partners to log in.
-
Copy and paste the Nubeva token.
Deployment steps
Sign in to your AWS account
-
Sign in to your AWS account at https://aws.amazon.com with an IAM user role that has the necessary permissions. For details, see Planning the deployment earlier in this guide.
-
Confirm that your AWS account is configured correctly and that you have your Nubeva token, as discussed in the Preequisites section.
Launch the Quick Start
| You are responsible for the cost of the AWS services used while running this Quick Start reference deployment. There is no additional cost for using this Quick Start. For full details, see the pricing pages for each AWS service used by this Quick Start. Prices are subject to change. |
Each deployment takes about 30 minutes to complete.
-
Sign in to your AWS account, and choose one of the following options to launch the AWS CloudFormation template. For help with choosing an option, see deployment options earlier in this guide.
If you’re deploying Nubeva SKI into an existing VPC, make sure that your VPC has two private subnets in different Availability Zones for the workload instances, and that the subnets aren’t shared. This Quick Start doesn’t support shared subnets. These subnets require NAT gateways in their route tables, to allow the instances to download packages and software without exposing them to the internet. Also, make sure that the domain name option in the DHCP options is configured as explained in the Amazon VPC documentation. You provide your VPC settings when you launch the Quick Start.
-
Check the AWS Region that’s displayed in the upper-right corner of the navigation bar, and change it if necessary. This is where the network infrastructure for Nubeva TLS Decrypt is built. The template is launched in the us-east-1 Region by default.
-
On the Create stack page, keep the default setting for the template URL, and then choose Next.
-
On the Specify stack details page, change the stack name if needed. Review the parameters for the template. Provide values for the parameters that require input. For all other parameters, review the default settings and customize them as necessary. When you finish reviewing and customizing the parameters, choose Next.
-
On the Configure stack options page, you can specify tags (key-value pairs) for resources in your stack and set advanced options. When you finish, choose Next.
-
On the Review page, review and confirm the template settings. Under Capabilities, select the two check boxes to acknowledge that the template creates IAM resources and might require the ability to automatically expand macros.
-
Choose Create stack to deploy the stack.
-
Monitor the status of the stack. When the status is CREATE_COMPLETE, the TLS Decrypt deployment is ready.
-
To view the created resources, see the values displayed in the Outputs tab for the stack.
Test the deployment
By default, this Quick Start includes TLS clients that generate standard web traffic and simulated attacks. Also, VPC traffic mirrors are created between a client and its respective tool. To validate the deployment and view the simulated threats, follow these steps. Each tool should be accessed directly.
-
Arkime: For alerts, connect to the interface using the link listed on the output of the CloudFormation stack.
-
Wireshark: Connect to the Wireshark console using the link listed on the output of the CloudFormation stack: https://elbaddress:14500. The default user name and password are wireshark/wireshark. Monitor the nurx0 interface for decrypted cloud traffic.
| This tool uses the default credentials. Note that Tooladmin/Toolpassword credentials are not supported. |
-
Suricata: For alerts, connect to the Kibana interface using the link listed on the output of the CloudFormation stack.
-
Zeek: For alerts, connect to the Kibana interface using the link listed on the output of the CloudFormation stack.
FAQ
Q. I encountered a CREATE_FAILED error when I launched the Quick Start.
A. If AWS CloudFormation fails to create the stack, relaunch the template with Rollback on failure set to No. This setting is located under Advanced in the AWS CloudFormation Management Console on the Options page. With this setting, the stack’s state is retained and the instance is left running, so you can troubleshoot the issue. (For Windows, look at the log files in %ProgramFiles%\Amazon\EC2ConfigService and C:\cfn\log.)
| When you set Rollback on failure to Disabled, you continue to incur AWS charges for this stack. Make sure to delete the stack when you finish troubleshooting. |
For additional information, see Troubleshooting AWS CloudFormation on the AWS website.
Q. I encountered a size limitation error when I deployed the AWS CloudFormation templates.
A. Launch the Quick Start templates from the links in this guide or from another S3 bucket. If you deploy the templates from a local copy on your computer or from a location other than an S3 bucket, you might encounter template size limitations. For more information about AWS CloudFormation quotas, see AWS CloudFormation quotas in the AWS documentation.
Troubleshooting
Follow these steps:
-
Check DynamoDB for keys. If you have items in the DynamoDB table, then at least one sensor is extracting keys and forwarding them.
-
Check client Docker logs by running the following command:
docker logs nubeva-agent -
Check Decryptor Docker logs by running the following command:
docker logs nubeva-rx -
Check Decryptor interfaces by running the following command:
ifconfig
Customer responsibility
After you successfully deploy this Quick Start, confirm that your resources and services are updated and configured — including any required patches — to meet your security and other needs. For more information, see the AWS Shared Responsibility Model.
Parameter reference
| Unless you are customizing the Quick Start templates for your own deployment projects, keep the default settings for the parameters labeled Quick Start S3 bucket name, Quick Start S3 bucket Region, and Quick Start S3 key prefix. Changing these parameter settings automatically updates code references to point to a new Quick Start location. For more information, see the AWS Quick Start Contributor’s Guide. |
Send us feedback
To post feedback, submit feature ideas, or report bugs, use the Issues section of the GitHub repository for this Quick Start. To submit code, see the Quick Start Contributor’s Guide.
Quick Start reference deployments
See the AWS Quick Start home page.
GitHub repository
Visit our GitHub repository to download the templates and scripts for this Quick Start, to post your comments, and to share your customizations with others.
Notices
This document is provided for informational purposes only. It represents AWS’s current product offerings and practices as of the date of issue of this document, which are subject to change without notice. Customers are responsible for making their own independent assessment of the information in this document and any use of AWS’s products or services, each of which is provided “as is” without warranty of any kind, whether expressed or implied. This document does not create any warranties, representations, contractual commitments, conditions, or assurances from AWS, its affiliates, suppliers, or licensors. The responsibilities and liabilities of AWS to its customers are controlled by AWS agreements, and this document is not part of, nor does it modify, any agreement between AWS and its customers.
The software included with this paper is licensed under the Apache License, version 2.0 (the "License"). You may not use this file except in compliance with the License. A copy of the License is located at http://aws.amazon.com/apache2.0/ or in the accompanying "license" file. This code is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either expressed or implied. See the License for specific language governing permissions and limitations.