HITRUST on AWS
Partner Solution Deployment Guide

August 2023
AWS Healthcare and AWS Infrastructure & Automation teams

| Refer to the GitHub repository to view source files, report bugs, submit feature ideas, and post feedback about this Partner Solution. To comment on the documentation, refer to Feedback. |
This Partner Solution was created by Amazon Web Services (AWS). Partner Solutions are automated reference deployments that help people deploy popular technologies on AWS according to AWS best practices. If you’re unfamiliar with AWS Partner Solutions, refer to the AWS Partner Solution General Information Guide.
Overview
This guide covers the information you need to deploy the HITRUST Partner Solution in the AWS Cloud.
AWS compliance architectures
AWS compliance solutions help streamline, automate, and implement secure baselines in AWS, from initial design to operational security readiness. They incorporate the expertise of AWS solutions architects and security and compliance personnel to help you build an automated architecture.
This Partner Solution includes AWS CloudFormation templates to automate building a baseline architecture that fits within your organization’s larger Health Information Trust Alliance Common Security Framework (HITRUST-CSF) program. It also includes HITRUST CSF security controls mapping, which maps HITRUST controls to architecture decisions, features, and the baseline configuration.
This deployment is for health IT infrastructure architects, administrators, compliance professionals, and DevOps professionals who want to implement or extend HITRUST workloads to the AWS Cloud.
Costs and licenses
There is no cost to use this Partner Solution, but you will be billed for any AWS services or resources that this Partner Solution deploys. For more information, refer to the AWS Partner Solution General Information Guide.
Architecture
Deploying this Partner Solution with default parameters builds the following HITRUST environment in the AWS Cloud.
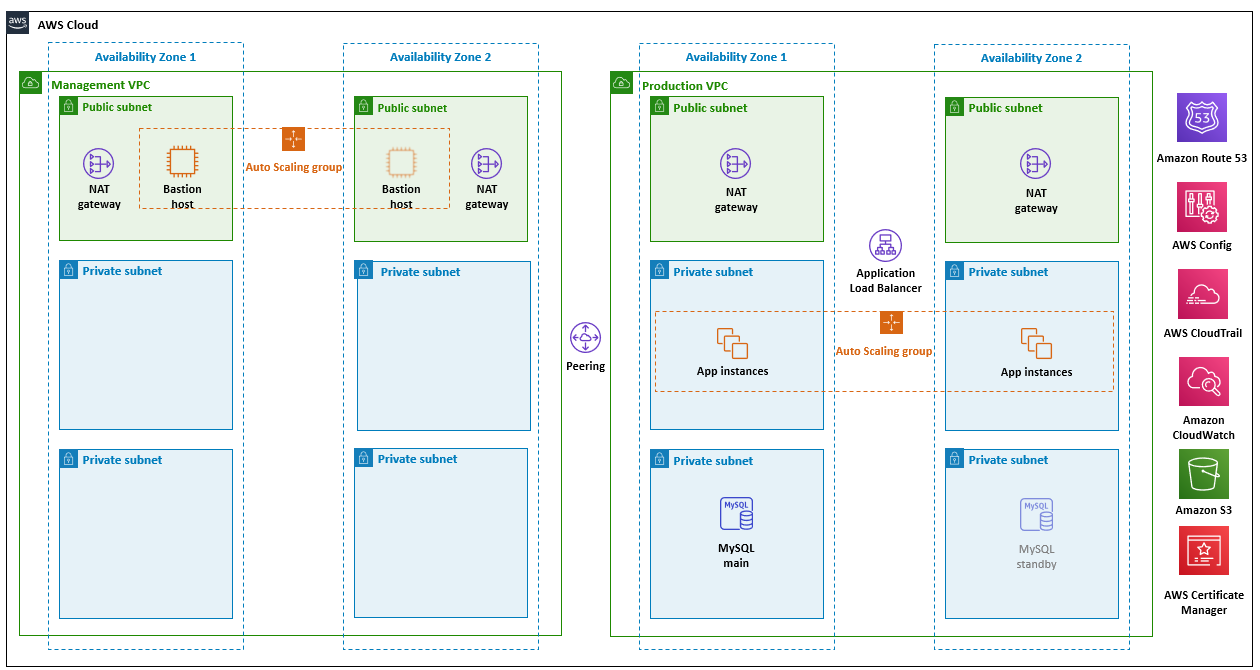
As shown in Figure 1, this Partner Solution sets up the following:
-
A highly available architecture that spans two Availability Zones.
-
A management virtual private cloud (VPC) and production VPC configured with public and private subnets, according to AWS best practices, to provide you with your own virtual network on AWS. The management and production VPCs have VPC peering enabled.
-
In the public subnets:
-
Managed network address translation (NAT) gateways to allow outbound internet access for resources in the private subnets.
-
In the management VPC, a Linux bastion host in an Auto Scaling group to allow inbound Secure Shell (SSH) access to Amazon Elastic Compute Cloud (Amazon EC2) instances in the private subnets.
-
-
Security groups for Amazon EC2 instances and load balancers, used in the sample application stack. The security groups limit access to only necessary services and disallow unencrypted traffic (for example, HTTP port 80).
-
An Amazon Simple Storage Service (Amazon S3) bucket for encrypted log content.
-
In the private subnets in the production VPC:
-
An encrypted Multi-AZ Amazon Relational Database Service (Amazon RDS) MySQL database and a standby instance in a second private subnet.
-
A three-tier Linux web application in an Auto Scaling group and an Application Load Balancer, which can be modified or bootstrapped with customer applications, such as WordPress.
-
-
A Secure Sockets Layer (SSL) certificate, managed by AWS Certificate Manager (ACM), on the load balancer to encrypt all traffic between the internet and load balancer. Separate self-signed certificates are generated on the Amazon EC2 instances to encrypt traffic between the load balancer and application instances.
-
AWS Config rules to monitor the deployment configuration. If you haven’t created a configuration recorder and delivery channel, this deployment creates them.
-
An Amazon Route 53 record set that maps the fully qualified domain name (FQDN) to the load balancer Domain Name System (DNS).
-
Logging, monitoring, and alerts using AWS CloudTrail, Amazon CloudWatch, and AWS Config rules.
Deployment options
This Partner Solution provides the following deployment options:
-
Deploy HITRUST into a new VPC. This option builds a new AWS environment that consists of the VPC, subnets, NAT gateways, security groups, bastion hosts, and other infrastructure components. It then deploys HITRUST into this new VPC.
This Partner Solution lets you configure Classless Inter-Domain Routing (CIDR) blocks, instance types, and HITRUST settings.
Predeployment steps
Prepare your AWS account
To deploy this Partner Solution, you must have your own domain name, and it must be managed by Amazon Route 53.
Deployment steps
-
Sign in to your AWS account, and launch this Partner Solution, as described under Deployment options. The AWS CloudFormation console opens with a prepopulated template.
-
Choose the correct AWS Region, and then choose Next.
-
On the Create stack page, keep the default setting for the template URL, and then choose Next.
-
On the Specify stack details page, change the stack name if needed. Review the parameters for the template. Provide values for the parameters that require input. For all other parameters, review the default settings and customize them as necessary. When you finish reviewing and customizing the parameters, choose Next.
Unless you’re customizing the Partner Solution templates or are instructed otherwise in this guide’s Predeployment section, don’t change the default settings for the following parameters: QSS3BucketName,QSS3BucketRegion, andQSS3KeyPrefix. Changing the values of these parameters will modify code references that point to the Amazon Simple Storage Service (Amazon S3) bucket name and key prefix. For more information, refer to the AWS Partner Solutions Contributor’s Guide. -
On the Configure stack options page, you can specify tags (key-value pairs) for resources in your stack and set advanced options. When you finish, choose Next.
-
On the Review page, review and confirm the template settings. Under Capabilities, select all of the check boxes to acknowledge that the template creates AWS Identity and Access Management (IAM) resources that might require the ability to automatically expand macros.
-
Choose Create stack. The stack takes about 30 minutes to deploy.
-
Monitor the stack’s status, and when the status is CREATE_COMPLETE, the HITRUST deployment is ready.
-
To view the created resources, choose the Outputs tab.
Postdeployment steps
Test the deployment
-
Navigate to the landing page. In the Outputs tab, choose LandingPageURL. The following webpage appears:
-
Confirm that WordPress is installed correctly. Note the application’s URL, and navigate to
ApplicationURL/wordpress/. If you want to set up the site, enter the requisite information. -
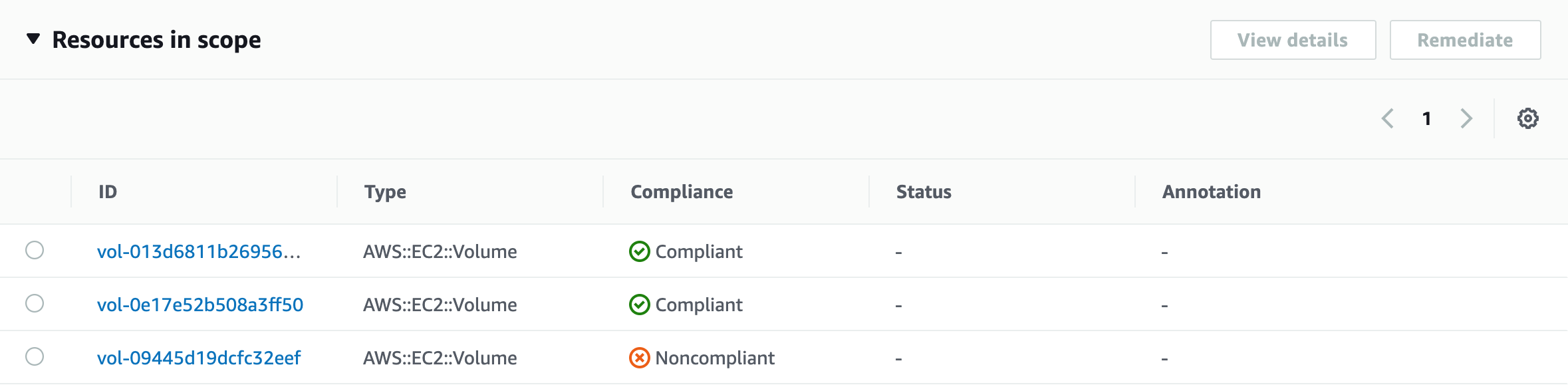
Navigate to the AWS Config console, where you can see the configuration status. Note that AWS Config monitors all resources in the AWS Region you deploy in, not just what’s from this deployment. For example, an Amazon Elastic Block Store (Amazon EBS) volume may not be encrypted elsewhere.
-
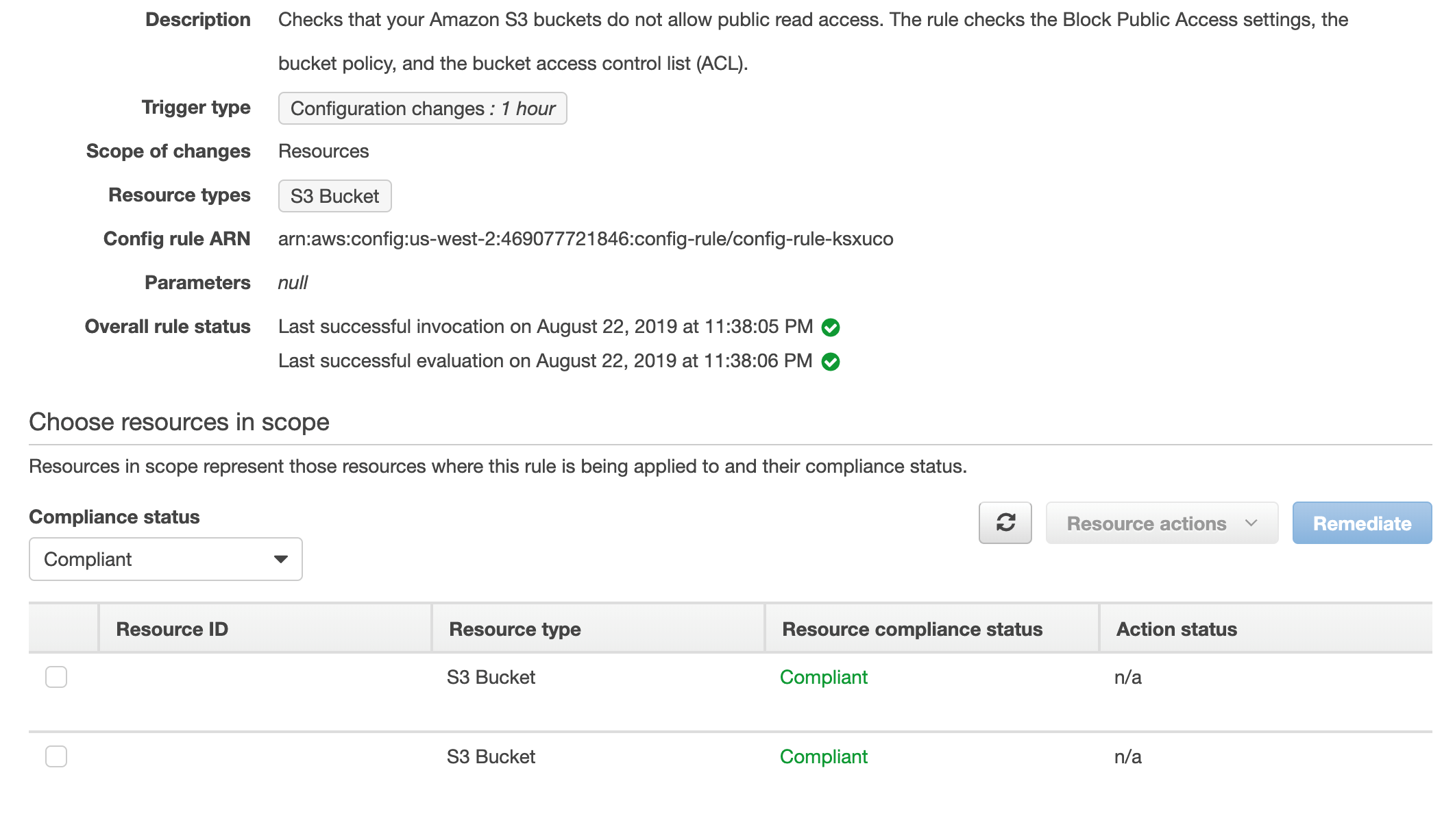
Disable read access for your Amazon S3 buckets.
Troubleshooting
For troubleshooting common Partner Solution issues, refer to the AWS Partner Solution General Information Guide and Troubleshooting CloudFormation.
Customer responsibility
After you deploy a Partner Solution, confirm that your resources and services are updated and configured—including any required patches—to meet your security and other needs. For more information, refer to the Shared Responsibility Model.
Feedback
To submit feature ideas and report bugs, use the Issues section of the GitHub repository for this Partner Solution. To submit code, refer to the Partner Solution Contributor’s Guide. To submit feedback on this deployment guide, use the following GitHub links:
Notices
This document is provided for informational purposes only. It represents current AWS product offerings and practices as of the date of issue of this document, which are subject to change without notice. Customers are responsible for making their own independent assessment of the information in this document and any use of AWS products or services, each of which is provided "as is" without warranty of any kind, whether expressed or implied. This document does not create any warranties, representations, contractual commitments, conditions, or assurances from AWS, its affiliates, suppliers, or licensors. The responsibilities and liabilities of AWS to its customers are controlled by AWS agreements, and this document is not part of, nor does it modify, any agreement between AWS and its customers.
The software included with this paper is licensed under the Apache License, version 2.0 (the "License"). You may not use this file except in compliance with the License. A copy of the License is located at https://aws.amazon.com/apache2.0/ or in the accompanying "license" file. This code is distributed on an "as is" basis, without warranties or conditions of any kind, either expressed or implied. Refer to the License for specific language governing permissions and limitations.